In an increasingly interconnected digital world, where data travels at the speed of light, are you truly securing your digital assets?
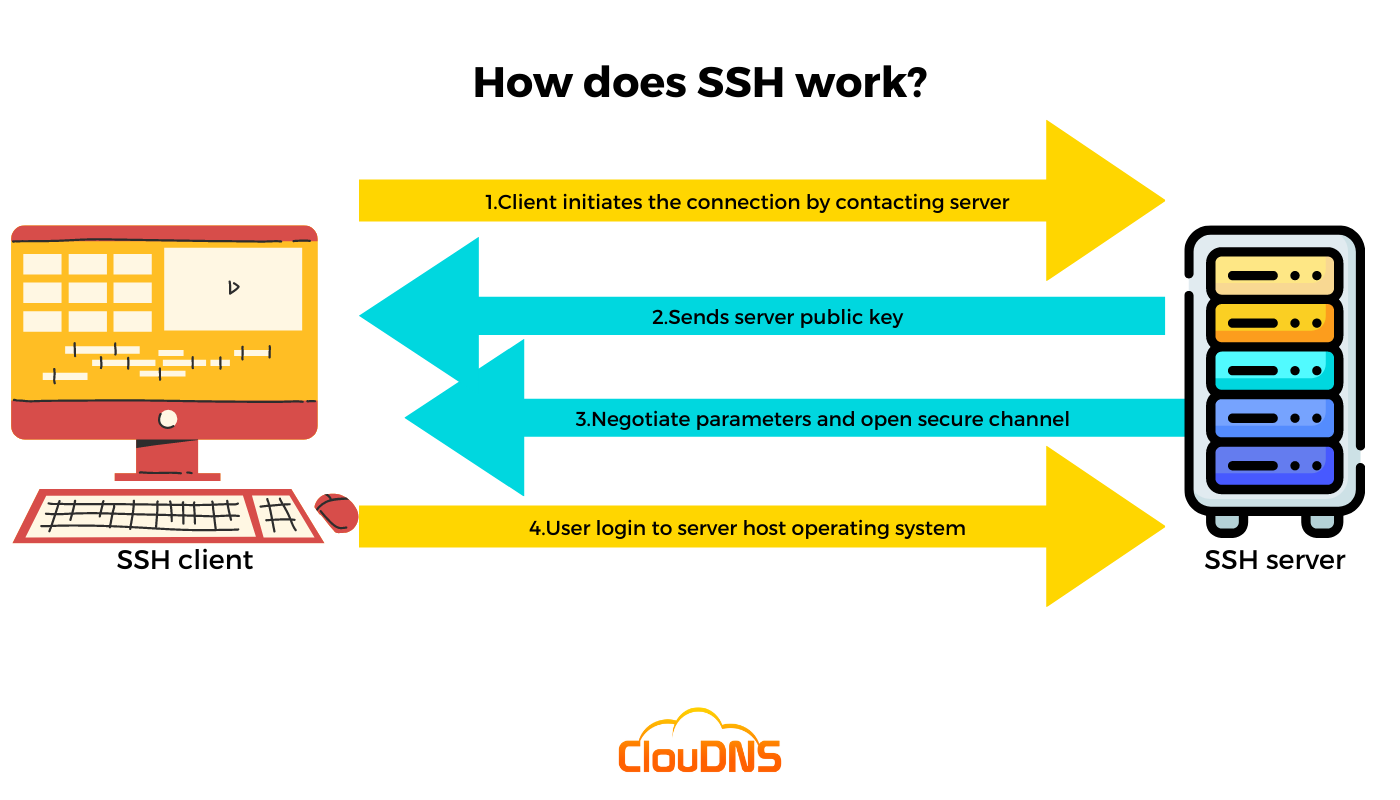
The Secure Shell (SSH) protocol, and its associated Secure File Transfer Protocol (SFTP), are not just technical jargon; they are the digital gatekeepers of your remote system management and data transmission. SSH is a robust network protocol, designed to facilitate secure remote login, file transfer, and more, making it a cornerstone of secure online interactions. The inherent security of SSH stems from its implementation of encryption and its utilization of public key authentication, making it a trusted method for managing systems remotely and for transferring data securely, provided it's configured correctly.
SFTP, or SSH File Transfer Protocol, is the most widely used secure file transfer protocol today. It operates over SSH and builds on SSH to facilitate secure file transfers. The relationship is essential: SFTP requires the SSH framework to operate, and while SSH can function independently, SFTPs very functionality relies on SSH's secure channel. SSH's ability to use port tunneling and forwarding, alongside its encryption methods, ensures that arbitrary data is transmitted securely, protecting it from the vulnerabilities of insecure networks.
| Aspect | Details |
|---|---|
| Protocol Name | Secure Shell (SSH) / Secure File Transfer Protocol (SFTP) |
| Purpose | SSH: Secure remote access and management. SFTP: Secure file transfer. |
| Relationship | SFTP operates over SSH. |
| Security Features | Encryption, public key authentication, port tunneling, and forwarding. |
| Encryption Method | Asymmetric encryption (private and public keys). |
| Key Protection | Private key kept by the owner; public key can be shared. |
| Configuration | Requires proper configuration to be secure. |
| Root Login | Best practice: Disable direct root login. |
| Standard User Accounts | Advised for initial login, then elevate privileges with su or sudo. |
| Configuration File | /etc/ssh/sshd_config (typically) |
| Service Restart Command | sudo systemctl restart sshd or similar, depending on the system. |
| Multiplexing | SSH supports multiplexing multiple data streams over a single TCP connection, improving efficiency. |
| Additional Uses | Terminal access, tunneling applications, forwarding TCP ports and X11 connections. |
| Potential Risks | Unsecured configurations can leave systems open to attack. |
| Common Vulnerabilities | Weak password, misconfigured settings, vulnerabilities in SSH server software. |
| Best Practices | Use strong passwords, enable key-based authentication, disable root login directly, keep software up to date. |
| Example Command - Connect to a server | ssh username@server_ip_address |
| Example Command - File Transfer via SFTP | sftp username@server_ip_address |
| Website Reference | SSH Protocol Documentation |
The process of setting up a secure connection usually begins by connecting to the remote server. This often involves being prompted for your login password on the remote host, unless key-based authentication has been set up.
Securing SSH access to your server is a critical step toward protecting your data. Default settings might function, but they often expose your server to threats. SSH is your digital gateway for the remote management of your Linux server, and if left vulnerable, it's an open invitation for attackers. Your servers security is directly proportional to how well you protect SSH. By securing SSH, you are preventing unauthorized access, data theft, and the disruption of your operations. Improperly secured connections provide a point of entry for malicious actors to wreak havoc on your infrastructure. The key to securing SSH lies in a layered approach that starts with understanding the protocol's fundamentals.
The SSH command is fundamentally designed to create an encrypted connection between two hosts over any network. This secure connection serves multiple purposes, including terminal access, file transfers, and tunneling for other applications, providing a secure conduit for a variety of tasks. Moreover, graphical X11 applications can also be run securely over SSH from a remote location.
- Best Kannada Movies 2025 Watch Legally Safely Avoid Movierulz
- Jameliz Benitez Smith Unveiling The Rising Social Media Star
At the heart of SSH is its utilization of encryption to protect the connection between a client and a server. All user authentication, commands, output, and file transfers are encrypted, forming a shield against potential attacks within the network. For anyone needing a deeper dive into how the protocol works, the comprehensive protocol page offers detailed information. The SSH protocol's core function relies on cryptography to establish a secure channel over an insecure network, thereby ensuring confidentiality and integrity of all data transmitted.
When using SSH to connect to a server, you establish a secure connection between your client (your computer) and the server (the remote computer you want to access). This encrypted channel means that everything that passes between your client and server is protected, reducing the chances of unwanted intrusions. Several important use cases highlight the value of SSH in the modern digital landscape.
The inherent security of SSH, which comes from its encryption and public key authentication, is a critical aspect to understand. SSH utilizes asymmetric encryption, which involves a pair of keys: a private key that is kept secure by its owner and a public key that can be shared. Anything encrypted with the public key can only be decrypted by the private key. This principle is essential in authentication and secure data exchange, providing a robust defense against various cyber threats.
The configuration of SSH servers presents both opportunities and challenges. Hosting an SSH server allows for remote connections from SSH clients, which increases the usefulness of your system. However, unless you configure security properly, anyone can connect to your system and attempt a login, which could lead to serious risks. Securing your SSH server is about preventing unauthorized access, data breaches, and operational disruptions.
One of the biggest challenges facing SSH security is related to certificates. Many companies give out secure keys for SSH connections, and databases containing these keys have been targeted by hackers. Protecting your SSH keys becomes paramount for the security of the infrastructure. The security of the keys is the primary line of defense against potential attacks. Any compromise of the private key compromises your entire system.
The best practice of securing SSH involves several steps:
- Disable Root Login Directly: Edit the configuration file, typically /etc/ssh/sshd_config, and change the value of `PermitRootLogin` from `yes` to `no`. This prevents direct login as the root user via SSH.
- Use Standard User Credentials: Log in with a standard user account and then use `su` or `sudo` to elevate your privileges.
- Implement Key-Based Authentication: This increases security versus password authentication.
- Change the Default SSH Port: Consider changing the default port (22) to make it less obvious for attackers.
- Enable Two-Factor Authentication: This is an extra layer of security that requires a code from an authenticator app in addition to the password.
- Firewall Rules: Use firewall rules to restrict SSH access to specific IP addresses or networks, further controlling who can connect to your server.
Restarting the SSH service after changing the configuration file is essential to apply the changes, which can usually be done using a command such as `sudo systemctl restart sshd`. By using these approaches, one can establish a powerful defense against unauthorized access.